EIP register not affected to buffer of send. To look into SEH, choose view > SEH chain
that the buffer has sent into the stack. For see data which is into application memory, right click line stack > follow in dump
copying file vbajet32.dll in system backtrack. File vbajet32.dll on windows, you can looking in windows > system32 > vbajet32.dll
Open metasploit at comand prompt filewith cd /pentest/exploit/framework
type:
For search POP, POP RETN in module, open OllyDbg click view > Executable module > double click vbajet32.dll at fil. After that right click > Search for > Sequence of commands
input POP r32, POP r32, and RETN
Now OllyDbg has found address in the memory vbajet32.dll
Copy pattern_create.rb into script and run script again. BigAnt has been crash. Note value at EIP.
Open terminal and search pattern_offset with value contained in the EIP
Type script this below
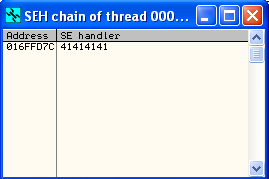
Script sucessfully executed, buffer value \x41 success entry into SEH handler
Type script below to enter address offset from vbajet32.dll
See that the process has break by OllyDbg exactly when it will access the address 0FA196A
looking SEh chain
push shift + f9 to countinue prosses in memory vbajet32.dl
To see memory address a great, right click on the first address of the "012CFD7C" > follw in dump > selection
Run msfweb on terminal
get payload into metasploit
Run script and find SEH Chain
Iam try to run script and result is :
and a know this payload any bad character. Iam reply to build payload with how to clean bad character "\x20\x25"
Reply copy payload this below to script:
run again this script
and now see the result



























Tidak ada komentar:
Posting Komentar