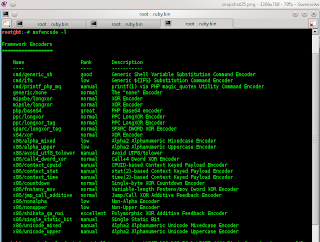
to use msf encode you must open terminal and type
- #msfencode -l
change directory to msf3 after that one of the easiest ways to use msfencode is to just directly pipe the output from msfpayload to it. After you determine which encoding method you want to use, you then determine which format you want to receive the result in similiar to msypayload. for example, we will use the x86/shikata_ga_nai encoder and output to another executable. the result is
- msfpayload is component of metaspolit alllows to generate shellcode, executable, and much more for use in exploit outside of the framework. Shellcode can be generated in many formats including C, Ruby , JavaScript, and even Visual basic for Application. Each output format will be useful in various situations.
To use msf encode you must open terminal and type
- #msfconsole -l
Type scrpit this below to listening and determining payload

where is msfencode from your title?
BalasHapus